Articles
The Impact of Geopolitics on Supply Chain Strategies
Reputational Risk Examples in Business: Common Ways Companies Lose Trust
If you are searching for reputational risk examples, you are probably trying to avoid the kind of surprise that does not show up in a spreadsheet until it is too late. A relationship can look fine on paper, then a hidden controversy turns into your problem, your...
What Is Reputational Risk in Corporate Due Diligence?
Reputational risk in corporate due diligence is the risk that working with a company damages trust in your business, because stakeholders form a negative view of who you are linked to. That perception can turn into real harm, such as lost deals, stricter scrutiny,...
What Is Corporate Due Diligence and When Do You Need It
When you are evaluating a new company to work with, the risk is rarely just about money. A bad counterparty can create legal exposure, operational disruption, reputational damage, or regulatory scrutiny. Those problems usually appear after the contract is signed, when...
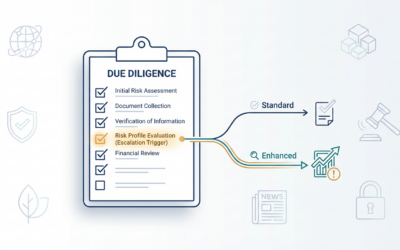
Corporate Due Diligence Checklist for Vendors and Partners
A corporate due diligence checklist is only useful if it helps you make a decision. You need questions you can actually ask, evidence you can request, and a clear rule for when to move from standard checks to enhanced due diligence. This guide gives you a copy ready...
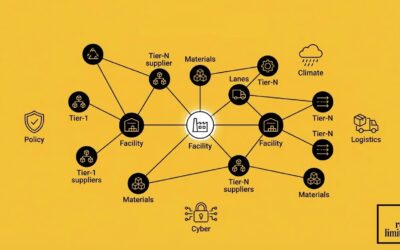
Risk Mapping & Scenario Planning in Global Supply Chains
Supply chains now face stacked risks: policy shifts, chokepoints, climate events, cyber incidents, and labor actions. Risk mapping shows where you are exposed across Tier-1 to Tier-N. Scenario planning shows what happens if something goes wrong, then compares...
Advanced Geopolitical Risk Assessment for Digital Due Diligence
Your vendors, cloud regions, and data routes live inside geopolitics. Elections, sanctions, and policy shifts can turn a "low risk" vendor into a stoppage in days. If you are buying due diligence or TPRM support, the geopolitical lens must be built in, not bolted on. ...
Top 13 Geopolitical Risks Affecting Your Supply Chain
Your vendors can be compliant on Monday and blocked by Friday. Sanctions expand, trade rules shift, and payment rails jam. If you buy, build, or ship across borders, you carry exposure. This page gives you a clear, ranked view of geopolitical issues, what to watch,...
Vendor Risk Checklist: Cybersecurity & Data Risk in Your Supply Chain Is this guide for you?
You run risk, compliance, or security at a mid-to-large organization. Vendors touch sensitive data or plug into your systems. You need a defensible way to judge their cybersecurity, privacy, and audit readiness. This guide gives you a practical checklist, the evidence...
Third-Party Risk Management: How to Keep Vendors from Becoming Cyber Liabilities
Vendors power growth, but they also bring hidden risks. A single weak supplier can expose sensitive customer data, interrupt daily operations, or trigger regulatory fines. Third-Party Risk Management (TPRM) gives businesses a proven way to spot these risks early and...
The Top 10 Cybersecurity Tools Every Supply Chain Risk Officer Should Know (2025–2026 Guide)
If you manage supply chain security, the right tools keep vendors and data safe. Supplier risk management platforms rate vendors, while threat intelligence flags new dangers. Vulnerability scanners catch weak spots, and SIEM connects logs to reveal attacks. IAM locks...
Is a third party you are dealing with high risk?
Find out in minutes.
Want a smarter more cost-effective way to deal with your third party risks?
Stay in the Know
Sign up to receive commentary on current events related to third party risk management.